So lets begin ...
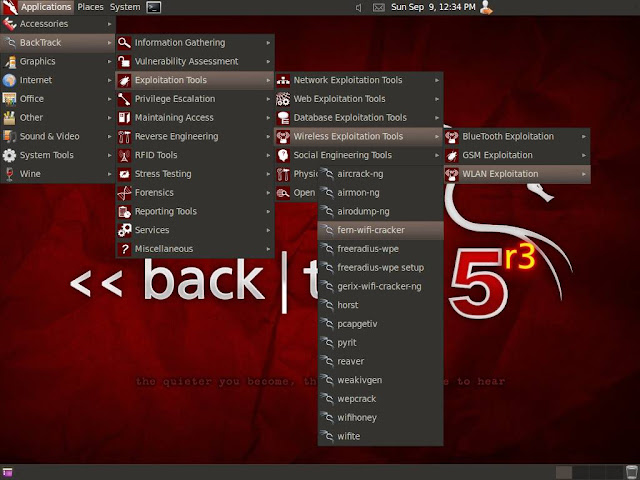
Go to backtrack --> exploitation tools --> wireless exploitation tools -->
WLAN exploitation --> fern-wifi-cracker
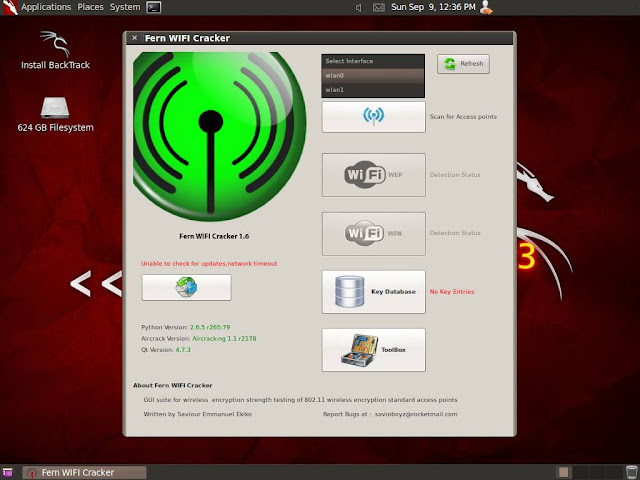
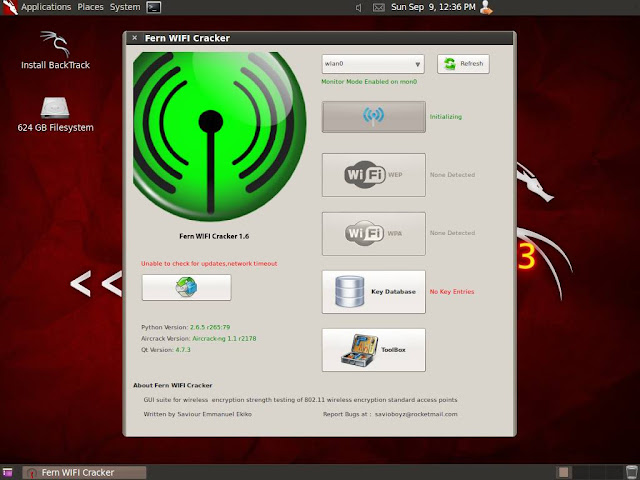
Now there's a button on which you can see wifi logo, click that and it will start the network scanning ( of-course its using airodump here).
Note*: if you double-click anywhere in the tool, you'll get a "settings" dialog box... you can set the channel there and also you can start the xterm.
Note*: if you double-click anywhere in the tool, you'll get a "settings" dialog box... you can set the channel there and also you can start the xterm.
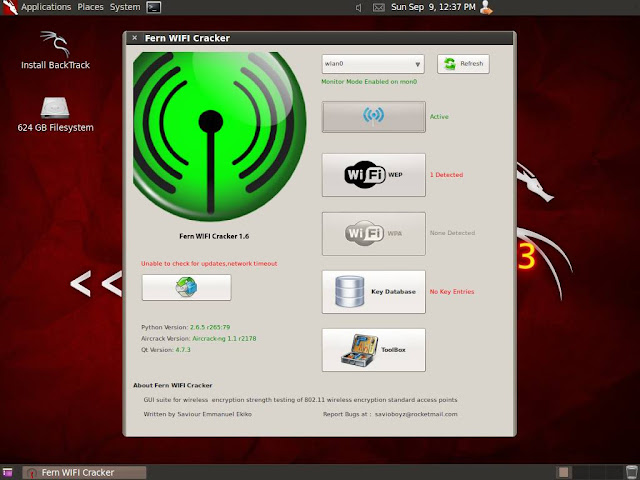
Now if you see closely, you'll note that the two buttons below the scan button will get enabled, the first button is the WEP cracking button and the second one is for WPA cracking.
Click the button for WEP cracking
Click the button for WEP cracking
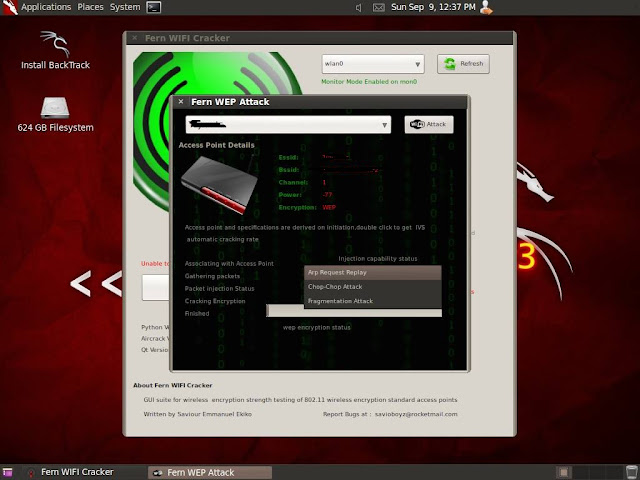
After clicking that button, a new dialog box will open. you can select the wep network from the list and then you can select the type of attack i.e arp replay attack, chop-chop attack or fragmentation attack. then click "Attack"...
When the password is cracked, it will be shown at the bottom of the dialog box...
NOW COMES THE INTERESTING PART:
(before going further, i suggest you to connect to the internet for this)
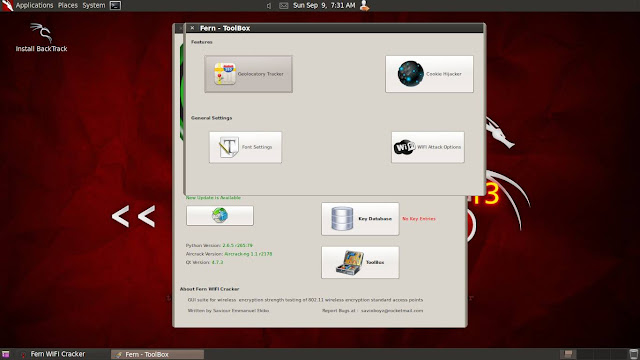
Go to "toolbox" --> Geolocatory tracker.
NOW COMES THE INTERESTING PART:
(before going further, i suggest you to connect to the internet for this)
Go to "toolbox" --> Geolocatory tracker.
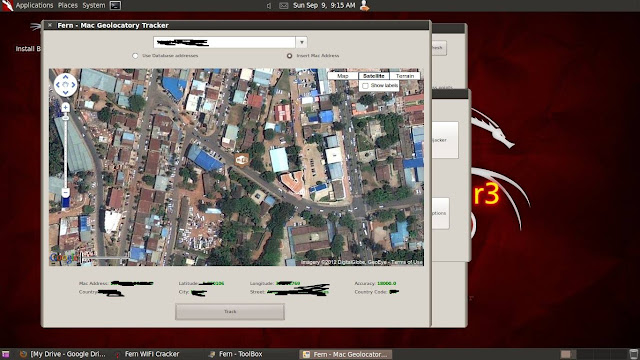
Give the bssid of the AP in the text box and click "Trace".
I think everyone has already guessed what it will show...
YES... INDEED... IT WILL SHOW YOU THE LOCATION OF THE AP ON THE GOOGLE MAPS ... You can see the coordinates as well..
YES... INDEED... IT WILL SHOW YOU THE LOCATION OF THE AP ON THE GOOGLE MAPS ... You can see the coordinates as well..











0 comments:
Post a Comment