Friday, May 31, 2013
Hacking The Interface Of Programs
This isn’t really a hack but a method to change the way program looks. It uses the Interface Builder used in applications to change the way a program looks. It is very simple, but if there is an annoying aspect of a program you just want to change, or to confuse your friends this is a fun way to start. With this trick you can’t hack every program, or every feature of a program. It is fun and a good time waster if you are bored.
The way to access the interface files is to the .nib file. This is the file type used to display and configure the interface you see. Most of the time this .nib file is wrapped up within the executable. But every so often you can get access to these files and change them. For this post I am going to use Mail. Find Mail in you Applications folder and show the package contents. Then navigate to Resources > English.lproj or any language you use. These are the localization files. It just happens that Mail has these files as seperate .nib files.
Make Your Own Dock
Hey
This post idea (and walk through) was written by Richard. It was pretty cool so I have decided to put it up. If you have any tips of your own that you would like to share please email me. This tip is very simple and fun to do. It is all about changing your dock background to something you have created. You can do this through Preview or through another image editing program like Photoshop.
The idea behind this trick is to change the background png files used in the dock to something we have created. These are only images so nothing to fancy. The first step is to back up the images we are going to change. Navigate to /System/Library/CoreServices/Dock.app/Contents/Resources. In this folder you should find scurve-sm, scurve-m, scurve-l and scurve-xl. Back these images up by creating a new folder in Resources (or anywhere you want) and copying these four images into it.
Change The Default Text For Anything
Hey
This post is a proper hacking post. It is designed to go into the core of the Mac OS X operating system and enable you to change some of the strings that control certain parts of text on your system. For example with this post you will be able to change the new folder name, as well as various other parts of your operating system. Once you get the hang of it you will be able to hack and crack your way to a computer system the way you like it.
Before we start I must stress that a lot of things can go wrong here. If you change the strings file incorrectly, the resulting application will probably crash, or everything you see will be garbled and unreadable. Do this at your own risk. It is safe as long as you insert your brain before you start anything. As always make sure you have a back up of the file your are going to change. I will point out which files you will need to back up as we proceed.
Install Movie Players in GNOME Backtrack 5
I like to hear songs while workign. If you are also like that, this article is for you. While usingbacktrack, you can use players.
For installing Totem media player,
Open the terminal(if you don't know how to open terminal, better don't use backtrack Linu).
Type the following command:
Enjoy.
For installing Totem media player,
Open the terminal(if you don't know how to open terminal, better don't use backtrack Linu).
Type the following command:
sudo apt-get install totem-gstreamerand hit enter, it will start to download files and install it.
Enjoy.
If you are using it from pen drive, verify you set enough persistence memory.
How to Install Teamviewer -Backtrack Tutorials and Tricks
Backtrack has all required tools for PenTesting. you caninstall Teamview in Backtrack also.
Teamviewer:
Teamviewer is legal Remote Administration Tool[RAT]. Using Teamview you can control your friend's system from your computer.
Visit Teamviewer official site:
http://www.teamviewer.com/en/download/index.aspxDownload .deb file
Copy it to desktop.
Open the Terminal
and type the following command:
sudo dpkg -i /root/teamviewer_linux.deb
It will install the Team viewer. Enjoy.
How to Hack the Windows Admin Password Using OphCrack in Backtrack tutorial
In this post, i am going to help you to crack the any type of windows accounts passwords. Learn how to hack the windows admin password like a geek.
This is My Second Backtrack Linux Tutorial.
Requirements:
- BackTrack Linux 4 or 5. Download it from http://backtrack-linux.org
- One pen drive(above 4gb)
- Xp Free Fast RainBow table [tables_xp_free_fast.zip]. Download it from here:http://ophcrack.sourceforge.net/tables.php
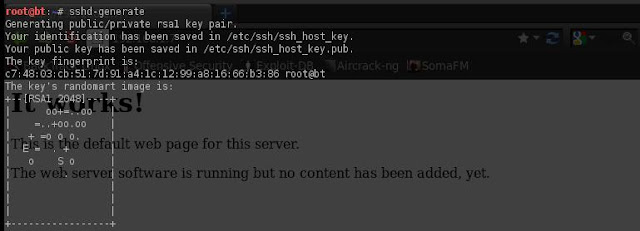
Enable SSH on Backtrack 5
Step 1:
root @ bt: ~ # sshd-generate
Step 2:
root @ bt: ~ # / etc / init.d / ssh start
Step 3 : Check if not succeeded root @ bt: ~ # netstat-ntlp Active Internet connections (only servers) Proto Recv-Q Send- Q Local Address Foreign Address State PID / Program name tcp 0 0 0.0.0.0:22 0.0.0.0: * LISTEN 3690/sshd
Installing BackTrack 5 Live On USB r2 and r3
Hello, Today i am going to Teach you, How to Install backtrack 5 r2 and r3 Live on USB. backtrack 5 r3 am also have same process. No Difference at All but in this tutorial i will use r2. came So the question in most minds of yours and why USB. It is Simple Quit Because it is portable, it work better than CD. CD got scratch and got bigger size than coal USB USB win in every manner. : P
[Sqlmap] SQL Injection using POST method
In this post short and simple, will detail the steps we will when we need to exploit a SQL Injection vulnerability, which are mostly based on some servers SQL Server and Oracle. These vulnerabilities are typical in LOGIN'S Administrative, because as we know, that when we enter the username and password this data is sent via the POST method, so there may be the possibility of entering false or some bypasses, this we can show an error that allows us to identify the vulnerability can be exploited so SqlMap running an automated using commands to send the request to POST and not GET as "usual".
If I did not explain well, for the few wise words! then no more bluntly, we take action!
We have an ASP LOGIN, which do not have the correct data or anything like that, since we have not found any vulnerability on a server that gives us this data, therefore we are curious and intelligent as we started testing false data and some bypasses as famosillo 'or '1' = '1 as shown in the following image:
Wednesday, May 1, 2013
When Databases Attack – Finding Data on SQL Servers
When Databases Attack – Finding Data on SQL Servers
Introduction
A few weeks ago I presented a webinar called “When Databases Attack”. It covered some SQL Server database configuration issues that are commonly overlooked and targeted by attackers. For those who are interested it can be viewed HERE. This is a response to some requests for script examples. In this blog I’ll provide a few scripts for finding sensitive data quickly in SQL Server. In the future I’ll provide scripts for other attacks as well.
A few weeks ago I presented a webinar called “When Databases Attack”. It covered some SQL Server database configuration issues that are commonly overlooked and targeted by attackers. For those who are interested it can be viewed HERE. This is a response to some requests for script examples. In this blog I’ll provide a few scripts for finding sensitive data quickly in SQL Server. In the future I’ll provide scripts for other attacks as well.
Finding Sensitive Data
There are a lot of great tools available for finding data quickly on a SQL Server. Some are commercial and some are open source. Most of them can be useful when gathering evidence during PCI penetration tests or when simply trying to determine if sensitive data exists in your database. In this section I’m going to cover how to find and sample data from SQL Servers using my TSQL script, and the Metasploit module based on the script.
TSQL Script – FindDataByKeyword.sql
This script will search through all of the non-default databases on the SQL Server for columns that match the keywords defined in the script and take a sample of the data. For more information please refer to the comments in the script.
Important Note: This script does not require SYSADMIN privileges, and will only return results for databases that the user has access to.
WordPress Asset-Manager PHP File Upload Vulnerability
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
require 'msf/core/exploit/php_exe'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::PhpEXE
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
require 'msf/core/exploit/php_exe'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::PhpEXE
Hacking Apps For Apple iPhone Devices
iPhone, an apple device with million copies and handed to people for nearly every field. This article focuses on the geeks out there looking for apps which could enhance their abilities and interest in hacking. Here are top 5 hacking apps for apple iPhone devices.
1). iKeyguard keylogger Hacking Apps For Apple iPhone
Mobile MITM Attack
What is Android?
To get a better understanding of what Android is capable of, we should first get a good handle on what it actually is.
In 2005, Google acquired a little known company called "Android, Inc", which had been developing software for mobile phones. Soon after, Google began filing various patents with a focus on mobile phone technology. This prompted the media to begin speculating that Google was planning on releasing a "G-Phone" to go head-to-head with Apple's immensely popular (and largely unchallenged) iPhone.
But in 2007, rather than announcing a single phone they intended to bring to market, Google brought together a group of some of the most important companies in the mobile industry and created the Open Handset Alliance (OHA), a consortium designed to develop open standards for mobile devices. The OHA revealed that their first product would be an open source mobile OS, called Android, designed to run on the full gambit of mobile devices (phones, tablets, netbooks, etc), rather than an OS tied to a specific piece of hardware (like Apple's iOS). In October of 2008, the HTC Dream (more commonly referred to as the G1) was released and became the first official Android device.
Android is made up of several software layers which are intended to make the OS more modular and easier to develop for. Android is based on the 2.6.x Linux kernel which handles hardware interaction, GNU userspace utilities for low-level system management, and various open source libraries such as OpenGL, SQLite, and FreeType.
How to Type Special Characters
If you often need to switch between the on-screen Alphabet and Number keyboards just to type a comma in a sentence, then why not check out below to find out more?
- , (comma) => touch and hold the Full-stop key (.)
- ' (single quotation mark) => touch and hold the Full-stop key, and slide to choose the single quotation mark (')
- " (double quotation mark) => touch and hold the Full-stop key, and slide to choose the double quotation mark (")
- Turn caps lock on/off => double-tap the Shift key to lock, single-tap to unlock.
- Special letters not on the keyboard? => touch and hold a key, then slide to choose a variation (See the screenshot).
- Need just a digit or symbol from the Number keyboard? => touch the ?123 key and slide to a digit or symbol key, and you're back to the Alphabet keyboard automatically.
Subscribe to:
Comments (Atom)











![Backtrack On Windows [via SSH] | Juno_okyo's Blog 1](https://dl.dropbox.com/u/35484167/1.png)