Many times I'll be at a site where I need remote support from someone who
is blocked on the outside by a company firewall. Few people realize that
if you can get out to the world through a firewall, then it is relatively
easy to open a hole so that the world can come into you.
In its crudest form, this is called "poking a hole in the firewall." I'll call it an SSH back door. To use it, you'll need a machine on the Internet that you can use as an intermediary.
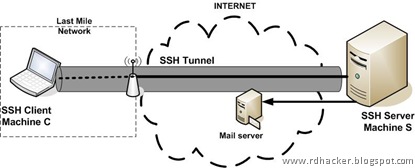
In our example, we'll call our machine blackbox.example.com. The machine behind the company firewall is called ginger. Finally, the machine that technical support is on will be called tech. Figure 4 explains how this is set up.
Figure 4. Poking a hole in the firewall

Here's how to proceed:
In its crudest form, this is called "poking a hole in the firewall." I'll call it an SSH back door. To use it, you'll need a machine on the Internet that you can use as an intermediary.
In our example, we'll call our machine blackbox.example.com. The machine behind the company firewall is called ginger. Finally, the machine that technical support is on will be called tech. Figure 4 explains how this is set up.
Figure 4. Poking a hole in the firewall

Here's how to proceed:























![[Image: Screen_shot_2011-02-24_at_11.34.20_PM.png]](http://cl.ly/0Y1j3z0S1D432b390z3Z/Screen_shot_2011-02-24_at_11.34.20_PM.png)
![[Image: disable-javascript-.jpg]](http://hackspc.com/wp-content/uploads/2011/02/disable-javascript-.jpg)
![[Image: all-javascript.jpg]](http://hackspc.com/wp-content/uploads/2011/02/all-javascript.jpg)

![[Image: BCXFD.gif]](http://i.imgur.com/BCXFD.gif)
![[Image: untitled24.JPG]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgGqHHASx-t3J791GN7ekCVklmoYAnGjL9tui41WMmJwFrNsVvzF_MgdXGAuMD1_CBU8_Bok-qQeFbhkm0hbLJeS5hP9jUJ4ll8XzRQgeRlpmMR_tC5wHzYVuJMsRPATv8JB9eUpym2Zyzh/s400/untitled24.JPG)



